Securing the Digital Watershed
Water Utilities are the New Front Line of Cyber Warfare
For decades, the mission of a water utility has been to apply a rigorous treatment process to a dynamic natural resource, ensuring safe water for our communities. We respect the source and trust our process to make it safe. That same clarifying principle must now be applied to the digital streams that govern our physical world.
The torrent of data flowing into our control rooms—from vendor updates to remote sensors—is a new kind of raw water, carrying with it invisible, sophisticated threats. Our digital watershed is under siege by state-sponsored adversaries, turning every utility into a front line in a low-cost, high-impact cyber war.
The shift has been gradual, then sudden. We moved from seeing water as a public utility to critical infrastructure. Now, we must accept its new reality as a national security imperative. The firewall is no longer the perimeter; it is merely the coarse intake screen, catching only the largest, most obvious debris. The real battlefield is deeper in the plant, inside the treatment process, inside the control room. Defense requires adopting the same mindset we use for water: assume the source is compromised and treat it accordingly, with the goal of producing not just potable water, but potable data fit for command.
The New Battlefield: Water's Strategic Importance
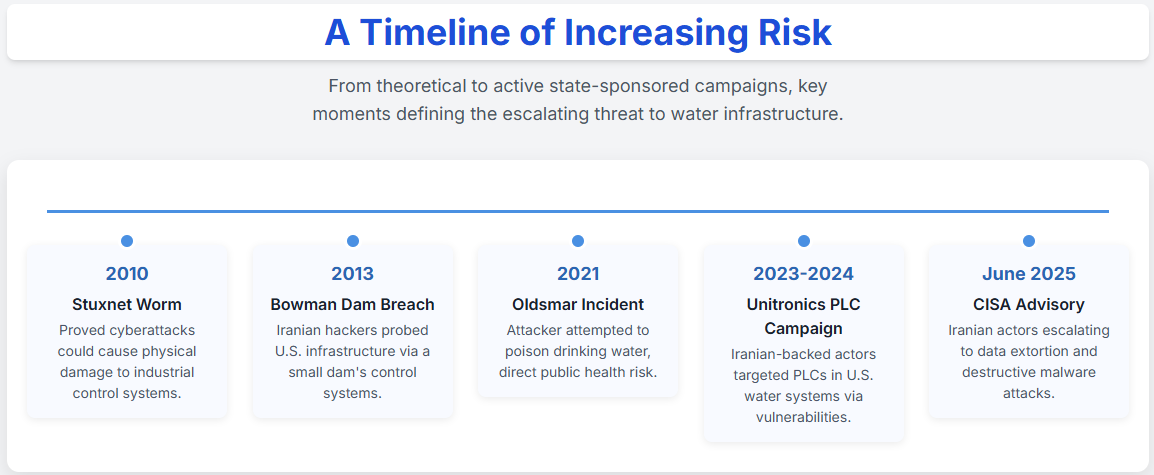
How did we get here? The evidence is no longer theoretical. The threat has escalated from the initial warnings about Iranian actors targeting Unitronics Programmable Logic Controllers (PLCs) in late 2023. In a June 2025 joint advisory, the Cybersecurity and Infrastructure Security Agency (CISA) and its partners detailed how these same government-sponsored groups are now leveraging known vulnerabilities for data extortion and deploying disk-encrypting malware against a broad range of sectors, including critical infrastructure. These weren't hypothetical scenarios; they were active, malicious compromises.
This is the tip of the iceberg. According to a recent enforcement alert from the Environmental Protection Agency (EPA), over 70% of inspected water systems are in violation of basic cybersecurity requirements, leaving them exposed. This widespread exposure isn't accidental; it's the result of a systemic misalignment of incentives and resources. For decades, utilities have been rewarded for focusing on physical infrastructure and keeping water rates low, making it difficult to justify major investments in "invisible" cybersecurity. This has led to a critical shortage of funding, a lack of specialized cybersecurity talent that can't compete with private sector salaries, and a "compliance-first" mindset that often lags behind the real-world tactics of adversaries.
The true danger, as CISA outlines, lies in interdependency. A disruption to a water utility isn't just an inconvenience; it can trigger a chain reaction of failures across other critical services. An attack threatens the operational capacity of hospitals and fire departments, can destabilize the energy grid, and grind entire regional economies to a halt. This elevates the mission beyond just ensuring clean drinking water; it becomes about upholding the stability of our entire societal ecosystem.
The Adversary Within (and Without): Understanding the Threat Landscape
To build an effective defense, we must first understand the adversary and the different threats they pose to different parts of our operations. While the business side of a utility (IT) is a frequent target for cybercriminals deploying ransomware for financial gain, the operational side (OT) faces a more dangerous and strategic threat. The primary threats to the physical safety and security of the water supply itself are not these financially motivated actors, but well-resourced, state-sponsored advanced persistent threat (APT) groups, with CISA specifically calling out actors from nations like Iran, Russia, and China.
Their motivations are strategic:
Asymmetric Warfare: For a relatively low cost and with minimal risk, they can inflict significant societal disruption, create panic, and undermine public trust in government.
Espionage: They seek to steal sensitive data, including engineering plans and operational procedures, to understand our infrastructure's weaknesses.
Pre-positioning: Perhaps most ominously, they aim to gain persistent access to our control networks, establishing a dormant presence that can be activated to cause physical damage during a future geopolitical conflict.
These adversaries are not breaking down digital walls with brute force. Instead, they are walking through doors we inadvertently left open. Their attack vectors are multifaceted, exploiting the very modernization that was meant to improve our systems. The drive for efficiency, globalized supply chains, and remote operational capability has created a new, complex threat landscape. Let's deconstruct the three primary pathways they use to move from the outside world into the heart of our operations.
1. IT/OT Convergence
How We Got Here: Historically, Operational Technology (OT) networks that control physical processes were "air-gapped" from business-focused Information Technology (IT) networks. The drive for efficiency and remote monitoring shattered this isolation, creating a digital bridge that inadvertently connected sensitive Industrial Control Systems (ICS) to the internet-facing corporate network.
The Core Problems:
Expanded Attack Surface: A single compromised IT asset can provide a direct pathway to core industrial controls.
Incompatible Security Paradigms: IT security prioritizes confidentiality, while OT prioritizes availability and safety, creating conflict in security procedures.
Insecure Legacy Systems: Many OT systems were never designed for network connectivity and cannot be easily patched.
The Strategic Solutions: Countering this requires re-establishing digital buffers through network segmentation, deploying OT-specific monitoring tools, and protecting legacy assets with compensating controls like unidirectional gateways.
2. Supply Chain Infiltration
How We Got Here: In the pursuit of cost savings, utilities sourced components from a globalized market, prioritizing price over security. This created opaque supply chains where hardware and software could be compromised at any point from the factory to the facility.
The Core Problems:
Embedded Malware: Adversaries can implant backdoors into PLCs, sensors, or other components before they are delivered.
Lack of Component Visibility: A system from a trusted vendor may contain critical microchips sourced from a high-risk, adversarial nation.
Hijacked Updates: A trusted vendor can be compromised, leading them to unknowingly push malicious software updates.
The Strategic Solutions: Mitigation depends on increasing transparency by demanding a Software Bill of Materials (SBOM), conducting rigorous procurement vetting that includes geopolitical risk, and implementing integrity monitoring to detect unauthorized changes.
3. The Human Element
How We Got Here: The need for remote access for employees and third-party vendors, combined with a lack of specific security training, created an environment where convenience often trumped security, leading to weak passwords and a high susceptibility to social engineering.
The Core Problems:
Credential Theft: Phishing remains the number one method for stealing employee credentials to gain initial access.
The Unintentional Insider: A well-meaning employee can inadvertently bypass security technology by clicking a malicious link.
Third-Party Risk: Granting remote access to vendors exposes the utility to attack if that vendor's own network is insecure.
The Strategic Solutions: The defense here is multi-layered, requiring a shift to a Zero Trust Architecture, implementing continuous, targeted training, and using Privileged Access Management (PAM) to control third-party access.
Beyond Compliance: Building a Resilient Hydro-Cyber Defense
For years, the water sector's approach to security was driven by compliance. This is no longer enough. The primary driver has been the America's Water Infrastructure Act (AWIA) of 2018, a federal regulation enforced by the U.S. Environmental Protection Agency (EPA). AWIA mandates that water systems serving over 3,300 people conduct a Risk and Resilience Assessment (RRA)—which includes cybersecurity—and submit it to the EPA every five years. This five-year cycle, while well-intentioned, can foster a "check-the-box" mentality that is dangerously out of sync with cyber threats that evolve daily.
While regulations have often lagged behind the threat landscape, a significant shift is underway, supported by new initiatives and resources:
New Legislation: The proposed Water Cybersecurity Enhancement Act of 2025 aims to provide direct grant funding for cybersecurity training and technical assistance.
Dedicated Funding Streams: The EPA now explicitly allows State Revolving Funds (SRF) to be used for cybersecurity, complemented by CISA's State and Local Cybersecurity Grant Program (SLCGP).
Hands-On Support: Programs like the USDA's "Cybersecurity Circuit Rider" program provide no-cost technical assistance to the most resource-constrained utilities.
Building a true hydro-cyber defense requires moving beyond compliance to a proactive, resilience-focused posture. The following CISA recommendations provide the tactical playbook for implementing the strategies needed to counter the threats identified above. Utilities can begin this journey today by leveraging CISA's no-cost pilot programs, such as their Free Cyber Hygiene Vulnerability Scanning service and their Cybersecurity Tabletop Exercise Packages (CTEP).
Segment IT and OT networks. To counter the risks of IT/OT convergence, create digital bulkheads. In a flat network, a compromise of a billing computer could pivot directly to the SCADA system. Proper segmentation, using firewalls and Demilitarized Zones (DMZs), forces an attacker to break through multiple, heavily monitored checkpoints, giving defenders crucial time to respond.
Implement robust, phishing-resistant Multi-Factor Authentication (MFA). To combat the human element of credential theft, use phishing-resistant MFA like FIDO2-compliant hardware keys. Unlike SMS texts or push notifications, these require a physical token that an attacker cannot access remotely, neutralizing the vast majority of credential-based attacks.
Aggressively patch and update all systems. To manage insecure legacy systems, adopt a risk-based approach. For a PLC that can't be easily patched, use "virtual patching"—configuring the network firewall in front of the device to block traffic that could exploit its vulnerability, shielding it until a scheduled maintenance window.
Disconnect OT devices from the public internet. There is almost never a valid reason for a PLC or Human-Machine Interface (HMI) to be directly accessible online. The Iranian attacks on Unitronics PLCs were successful because these devices were discoverable on search engines like Shodan. Removing that connection is the simplest defense against this attack vector.
Develop and regularly test a comprehensive incident response and recovery plan. A plan on a shelf is useless. It must be a living document tested through tabletop exercises that simulate realistic scenarios. An exercise might reveal that the emergency contact list for the FBI is outdated or that the OT team lacks credentials for the backup server. These drills identify critical gaps before a real crisis.
While these are critical, forward-looking leaders must think beyond the immediate checklist. True resilience will be built on a foundation of next-generation strategies:
"Trusted" Supply Chains: The future of water security will involve a deliberate push for "friend-shoring" and domestic development of critical technology. This isn't just a policy preference; it's a security necessity, underscored by the strategic implications of the CHIPS and Science Act. While not aimed directly at water utilities, the CHIPS Act is foundational to the security of all critical infrastructure. By incentivizing domestic semiconductor manufacturing, it enables an ecosystem of trusted, verifiable technology. For a utility leader, this fundamentally changes the calculus of procurement. The question is no longer just, "Does this PLC meet our technical specs?" but, "Can we verify the integrity of its components from the silicon level up?"
Example Secure Procurement Workflow:
Security-Focused RFI: Begin the process with a Request for Information (RFI) that prioritizes security. Ask vendors about their secure development lifecycle, their ability to provide a Software Bill of Materials (SBOM), and the geopolitical origin of their key components.
Geopolitical Risk Assessment: Evaluate the vendor and its primary suppliers for geopolitical risk. A low-cost component from a high-risk nation may carry an unacceptable security cost.
Contractual Mandates: Embed security into the contract. Include clauses that require immediate breach notification, the right to audit security practices, and the mandatory delivery of an SBOM with every software or firmware update.
Secure Onboarding: Upon delivery, verify the integrity of hardware and software. Scan all components for malware and establish a secure baseline before connecting them to the operational network.
Continuous Monitoring: The procurement process doesn't end at purchase. Continuously monitor the vendor for public breaches and the product for newly discovered vulnerabilities throughout its lifecycle.
AI/ML for Anomaly Detection: We must move from reactive alarms to predictive security. Artificial Intelligence and Machine Learning (AI/ML) algorithms can monitor water flow, pressure, and chemical levels to identify subtle anomalies that indicate a system compromise long before it becomes catastrophic.
Scenario: The "Slow Bleed" Attack. An attacker gains low-level access and slightly increases a valve opening by 0.5%—a change too small to trigger a standard alarm. A traditional system sees this as normal fluctuation. An AI/ML system, however, has learned the complex "rhythm" of the entire network. It detects this persistent 0.5% change doesn't correlate with any other system variable (pump speed, time of day, etc.) and flags it as a statistical anomaly, allowing an operator to investigate and stop a subtle attack before it escalates.
Cyber-Physical Fusion Centers: A traditional Security Operations Center (SOC) is blind to physical processes. Its analysts are trained to spot malicious network traffic, but they lack the context to understand what that traffic means for a pump, a valve, or a chemical doser. This creates a critical visibility gap where a sophisticated attack can be misinterpreted as a simple mechanical failure. The industry requires an evolution: the Cyber-Physical Fusion Center. This model merges two distinct worlds of expertise—IT security analysts and OT process control engineers—into a single, cohesive unit.
Scenario: Pipe Break or Cyberattack? An alarm shows a sudden pressure drop in a major distribution line. A traditional SOC sees no malicious traffic and dismisses it as a physical problem. A Fusion Center analyst, however, immediately correlates the pressure drop with a brief, unauthorized remote login to the PLC controlling a valve in that same section just seconds earlier. The fusion center doesn't see two separate events; it sees one unified, high-confidence cyber-physical incident, enabling a rapid, accurate response. A real-world model for the intelligence-sharing component of this concept is the Water Information Sharing and Analysis Center (WaterISAC), which provides sector-specific threat intelligence to its members.
Workforce Development: Technology alone is not a defense. A resilient organization is built on a security-conscious culture that extends from the control room to the front office. While there is a critical shortage of professionals trained in securing industrial control systems, workforce development must also focus on non-IT staff. Operators, technicians, and administrative personnel are the true front line; they must be trained and empowered to act as "human sensors," capable of identifying anomalies in both the physical and digital worlds. This requires a positive organizational culture where morale is high and employees feel valued—engaged staff are vigilant staff. Furthermore, security must be embedded in the hiring process, ensuring that new team members, regardless of role, are vetted and understand their critical responsibility in protecting the utility. This holistic approach aligns with the broader national strategy, including massive workforce development investments within the CHIPS and Science Act, to build the talent pipeline required for a secure industrial base.
Your System is a Target. What's Your Next Move?
The era of viewing water utilities as mundane infrastructure is over. The question is no longer if your system will be targeted, but when. This is not a call for panic, but for urgent, clear-eyed action. Investing in resilience is not a one-time fix; it is an ongoing arms race that demands continuous investment in people, processes, and adaptation.
After reading this, every leader in the water sector should be asking three questions:
When was the last time we pressure-tested our incident response plan against an attack that targets our people, not just our technology?
Do we know the geopolitical origin of our critical components, and have we contractually mandated security from our vendors?
Is our organizational culture creating vigilant "human sensors," or is it unintentionally fostering the next insider threat?
The answers will determine whether your utility remains a source of community stability or becomes the next headline.
A special thanks to Jeffrey Harp, CPP, Director of Security and Asset Protection at the SFPUC, for his invaluable feedback on this article.